VMC on AWS Outposts can leverage AWS Direct Connect private VIFs for the service link private connectivity. A set of Elastic Network Interfaces (ENIs) within an Amazon VPC is created to establish the service link connectivity to the AWS service anchor private endpoint. This Amazon VPC is created in the VMware-owned and managed AWS account in the AWS Region, and connectivity is established over an AWS Direct Connect private VIF. Organizations may also use an AWS Direct Connect Gateway (DXGW) for cross-Region Direct Connect access if necessary. However, it’s important to note that AWS Outposts private connectivity does not support using AWS Transit Gateway or site-to-site IPsec VPNs.
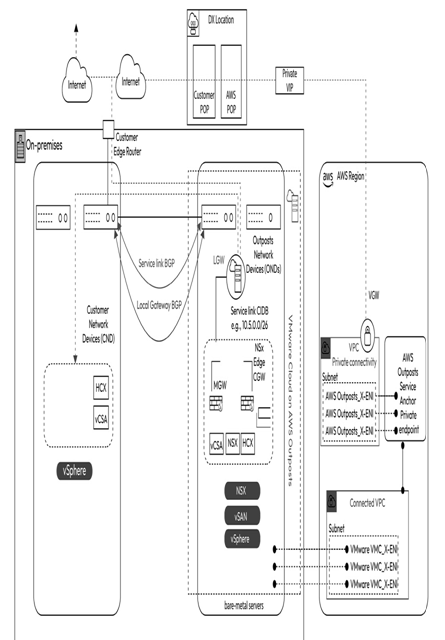
Figure 10.12 – VMware Cloud on AWS Outposts service link private connectivity
Figure 10.12 depicts VMC on AWS Outposts (on the left) connected to the AWS Outposts service anchor in the AWS Region via the service link private connectivity. The AWS Region (on the far right) contains a Virtual Private Gateway (VGW) attached to the Amazon VPC hosting the ENIs that connect to the AWS Outposts service anchor private endpoint.
Using the private connectivity option eliminates the need for the service link traffic to traverse the public internet. It also prevents organizations from having to use large public allow lists on their on-premises firewalls. This is because the AWS Outposts service anchor private endpoint now uses the ENIs in the VMware-owned Amazon VPC. It will also enable organizations to use AWS Direct Connect features to monitor the connectivity using Amazon CloudWatch metrics.
To ensure robust and resilient private connectivity, organizations should consider using redundant DX locations and DX partners. It is highly recommended to review AWS DX resiliency recommendations to choose a DX architecture that meets the organizations’ specific availability requirements.
Service link disconnection
Irrespective of whether you’re using private connectivity or public connectivity, VMC on Outposts is not designed for operating in disconnected mode for long durations. In the case of a network outage that results in the service link connectivity being disconnected, the following will occur:
- Virtual machines and VMware vSAN storage will continue to run and be accessible via the LGW
- API calls to the AWS Region will fail (downloading from the content library, creating new logical networks, and so on)
- Metrics will be spooled locally for a limited period
- If there is a host reboot as a result of a power outage, during a service link disconnection, VMware vSAN will be inaccessible for that host
VMC on AWS Outposts configuration
VMC on AWS Outposts streamlines IT operations by providing a fully managed solution. AWS takes care of delivering, installing, monitoring, patching, updating, and maintaining the Outposts hardware at the organization’s on-premises location. In addition, VMware ensures continuous LCM of VMware SDDC and provides direct first-party support. The following components are included with VMC on AWS Outposts:
- Standard 42U rack hosting AWS Outposts components
- Amazon Nitro-based EC2 bare-metal servers with local SSD storage
- VMware SDDC software including vSphere, vSAN, NSX-T, and vCenter Server
- VMware Hybrid Extension (HCX) Enterprise license
- VMware global support
While VMware Cloud on AWS supports a variety of EC2 bare-metal instance types including i3.metal, i3en.metal, and I4i.metal, VMware Cloud on AWS Outposts supports only the i3en.metal instances.
| Specifications | Amazon EC2 i3en.metal |
| Compute | |
| CPU type | Intel Xeon Cascade Lake (dual socket) |
| CPU cores | 48 cores @ 2.5 GHz (96 HT cores) |
| Custom core count | 8, 16, 24, 30, 36, or 48 |
| Memory | 768 GiB |
| Storage | |
| Type | vSAN with local NVMe All Flash |
| Capacity and optimization | ~45.8 TiB (raw) – compression enabled (40.35 TiB usable per host) |
| Network | |
| Physical speed | 100 Gbps (currently 50 Gbps supported) In-transit encryption on the NIC for east-west traffic |
Table 10.8 – Hardware specifications for Amazon EC2 i3en.metal instance type